PCI DSS FAQs
PCI DSS v4.X Frequently Asked Questions
Certain payment acceptance channels and/or methods have new requirements, and some have been removed. In addition, many of the existing requirements now include new controls. What will change for your business depends on your SAQ (Self-Assessment Questionnaire) type.
Your SAQ type will determine how these changes impact you. Guidance on your SAQ type is available here.
The compliance portal journey has been designed to factor in all changes and ensure that you are reporting against the latest version of the standard.
Once you have completed your business profile on the compliance portal, your SAQ type will be displayed on your dashboard under “Your business profile.” (See image below). It is important that you answer all questions as accurately as possible.
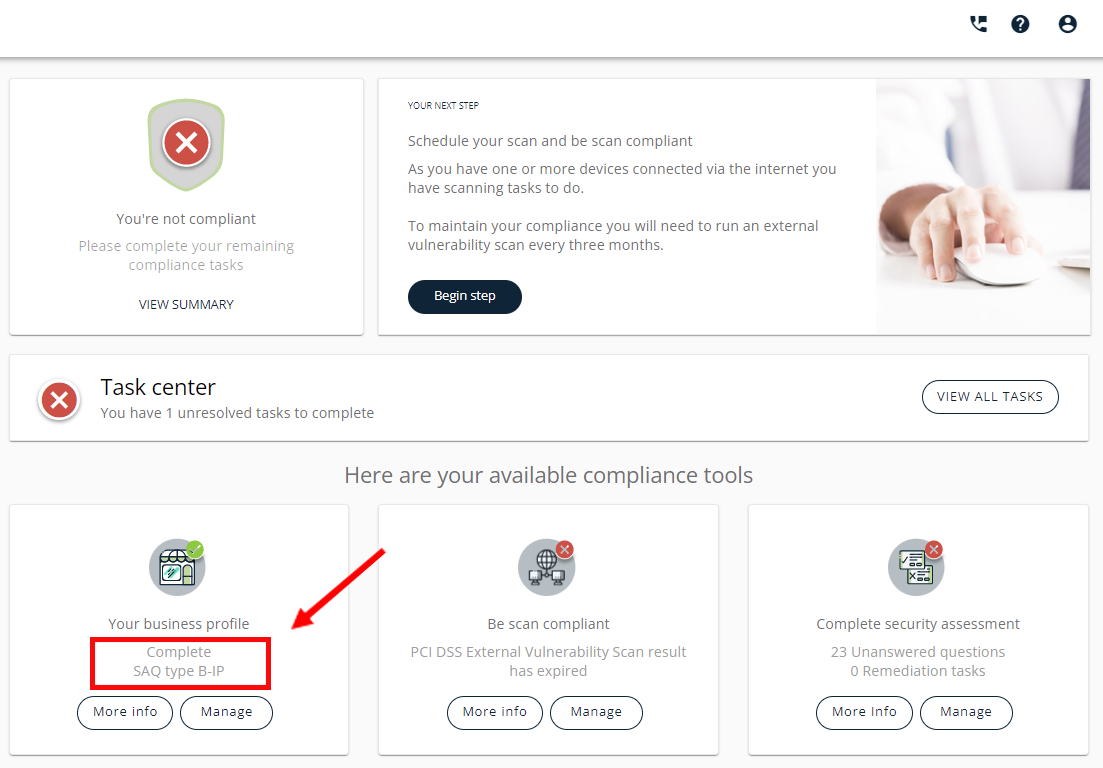
Image: Compliance portal dashboard showing SAQ Type. This example illustrates an SAQ type B-IP.
Your compliance portal will guide you through the changes. As you may have some new requirements, we recommend starting your assessment as early as possible before your renewal date. If you need additional assistance, your support options are available on your online portal or program email communications.
If you have started but not completed your compliance journey when new PCI DSS requirements relating to your SAQ type become effective, you will need to reprofile to determine the applicability of the new requirements to your business. While business profile questions will be populated with your previous answers, there may be new business profile questions for you to complete.
As new requirements become effective, assessing compliance with those requirements may take longer. The updates include more information about applicability and guidance that you may need to read through to better understand how the requirements will apply to your business.
It helps to be prepared in advance – know who to call regarding the set up and security of your payment systems e.g., your e-commerce website, point-of-sale system etc.
SAQ types that apply to e-commerce businesses, as well as those using point-of-sale systems or other payment application systems connected to the Internet, have several significant changes.
No. The period for which your SAQ assessment result is valid does not change when the version of the standard you assessed has been retired.
Only if your third party’s PCI DSS assessment was completed against a version of the PCI DSS that was still in effect at the time of that assessment and their assessment is still valid (i.e., it was completed within the last 12 months), then you may mark as “Not Applicable” those requirements for which you rely upon the TPSP but for which they have not yet been assessed.
The other scenario is where your TPSP assessment was completed before the effective date of the new requirements (April 1, 2025). Those future-dated new requirements – that the TPSP will be responsible for meeting on your behalf – were not included in their assessment. The TPSP may mark these as “Not Applicable,” in which case where they impact your assessment, you can also mark them as ”Not Applicable,” until the next time you and your TPSP need to complete your assessment.
There are a couple of FAQs that explain the scenarios here: FAQ 1282 and 1564.
Yes. All answers previously provided as part of your profile will be retained following the update so you can review what was previously submitted. You can change these answers as you progress through the profile if anything regarding how you store, process and/or transmit payment card data has changed. Depending on your processing methods and card data handling, you may be asked additional questions that may or may not change the outcome of your subsequent profile questions, SAQ type, SAQ auto-answering effects, and the requirement to perform External Vulnerability Scanning by an Approved Scanning Vendor (ASV) scanning on your environment.
After you complete your business profile, the portal determines what answers from your previous assessment can be mapped and applied to the same or similar question in the latest version so you do not need to answer those questions again.
- If you previously indicated that you are not compliant with a particular requirement, you will be required to re-assess and provide a response to that question again.
- On completion of your business profile, a new set of auto-answer effects will be applied to your current assessment based on the new rules defined for the latest version. If there are newly applicable requirements, you will need to review and provide your response as it applies to your business.
If your website uses a URL redirect/embedded iFrame and you are eligible to self-assess compliance using the SAQ A, you will need to complete an External Vulnerability Scan, also referred to as ASV scanning, as these scans need to be performed by a PCI- Approved Scanning Vendor (ASV). This is a non-intrusive website scan that helps identify vulnerabilities that may lead to a compromise of your website and customer card data.
If you are unsure if you need to scan and what to scan, please check with your web developer regarding how your website is set up to accept card payments. If scanning is required, you will receive detailed instructions.
If External Vulnerability Scanning applies to your website, you will need to scan at least once every 90 days – and whenever a significant change is made to your website or web servers to maintain your compliance with the PCI DSS.
Note: The target environment for External Vulnerability Scans must include your e-commerce servers that either redirect your customers to a hosted payment page for payment processing, or that embed the hosted payment page, form or fields in one or more iFrames.
Yes. Historical records relating to previously attested, completed/submitted SAQ and scan documentation will remain available from within the scan and SAQ widgets on your merchant dashboard as they are today.
Where applicable, policy templates have been updated. We recommend that you review your existing policy and associated procedure documents and update them if necessary.
Each question in the Self-Assessment Questionnaire (SAQ) has supporting guidance and applicability notes. If you need additional assistance, your support options are available on your online portal or program email communications.
The latest PCI DSS version, requirement 8.3.6, states that password (or passphrase) complexity must be 12 characters, with an exception for legacy systems permitting a minimum length of 8 characters. Passwords must contain numeric digits and alphabetic characters.
This SAQ question is presented to merchants in their SAQ for the following SAQ types: D, A-EP, C, C-VT, and A.
Recent changes by SAQ type are visible in the SAQ Explained section of this information website.
More resources:
The PCI SSC publishes regular guidance updates here:
https://www.pcisecuritystandards.org/faqs/all/ You can filter FAQs by publication date to see the most recent FAQs.
You can also search FAQs by keyword/topic and or FAQ number:
The PCI SSC also publishes information supplements and guidance documents in the Document Library:
https://www.pcisecuritystandards.org/document_library/ (filter by ‘Guidance Document’).
Topics include: ASV Resource Guide, Multi-Factor Authentication Guidance, Penetration Testing Guidance, Best Practices for Implementing a Security Awareness Program, Skimming Resource Guide, Best Practices for Securing E-commerce, PCI DSS Scoping, and Segmentation Guidance for Modern Network Architectures.
Need more help?
If you need additional assistance, your support options are available on your online portal or program email communications.
Or visit PCI DSS v4.X Resource Hub.
